Privacy battle on the horizon

The new internet protocol known as Multipath Transmission Control Protocol enables easy privacy invasion, but also secures today’s networks.
On the internet, your traffic is not your own -- no matter how you roam. New multipath technologies, including one found hidden dormant in the internals of the newest Mac operating system, OS X 10.10 Yosemite, may provide consumers with more tools to gain control of their online communications. However, this freedom comes at a price, which network operators may not be willing to pay.
Transmission Control Protocol (TCP) is one of the core protocols that almost all networked computing devices use when they need to communicate reliably. Every time you send an email, post to Twitter, check the weather, or even log into online banking, TCP silently manages your network communications. Most of the modern internet, and the internet connected world, depends on it but it has not changed all that much in the last 30 years -- until now.
Multipath TCP, a major enhancement to TCP, enables endpoints to use multiple internet connections in a communication seamlessly. This not only means it’s possible to spread traffic over them and access their combined speed, but also enables a system to shuffle traffic flows between paths.
This has potentially huge implications for privacy and net neutrality. It becomes more difficult for an internet service provider (ISP) or government to monitor your traffic easily, as if they do not get all paths it can be impossible to accurately determine content. Network neutrality also becomes more interesting too. If one internet connection mysteriously slows down your Netflix traffic then you can seamlessly switch to the other -- without dropping a frame.
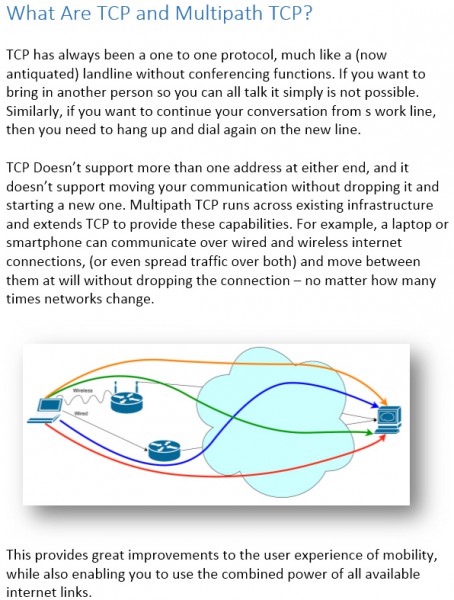 These seem like wonderful things, and indeed for consumer devices on ISP networks, they are. If, however, you are the one who operates a network, these same capabilities could become more than a little problematic. We are simply totally unprepared if malware or attackers start to take advantage of these techniques (whether MPTCP or not).
These seem like wonderful things, and indeed for consumer devices on ISP networks, they are. If, however, you are the one who operates a network, these same capabilities could become more than a little problematic. We are simply totally unprepared if malware or attackers start to take advantage of these techniques (whether MPTCP or not).
Here’s why: Network security as we practice it today relies heavily upon content inspection and source attribution.
Content Inspection
Today a very common approach is to look at traffic contents to decide whether it is malicious or not. In a multipath communication, you can only see a fraction of the traffic across any given route, making understanding what is traveling over a link much more difficult. With the ability to communicate in a way that’s much more difficult to detect, attackers who have set up a persistent backdoor on networks will be able to stay on compromised networks longer, and capture more private data.
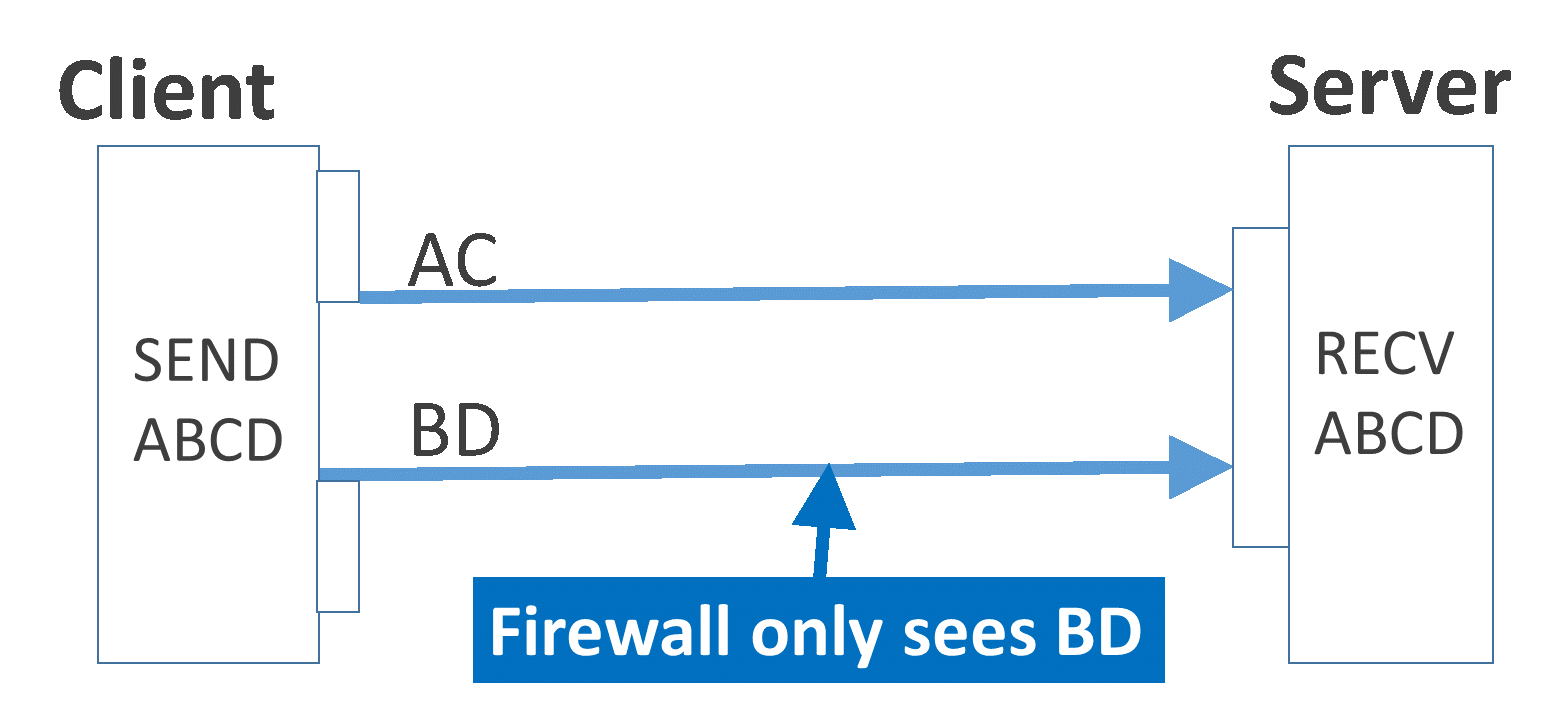
Splitting traffic over paths makes full content inspection impossible for a firewall on only one path.
Attacker Attribution
The mobility features of MPTCP enable systems to move around the Internet continually and seamlessly. This is great for your phone, but in a multipath world, it can be abused to make malware control systems far more difficult for law enforcement to track down and shut down.
Previously law enforcement has targeted malware command and control (C&C) systems to shut down whole botnets by chopping off their heads. Malware that uses address mobility, while also using and switching between a very large number of network connections in parallel, has the potential to overwhelm our ability to track down the people behind it while also negating a good amount of deterrent and making it a little safer for attackers.
One person’s powerful tool can be another’s powerful weapon -- the properties of today’s networks that enable easy privacy invasions are the same that we commonly use to secure networks. Do we have another battle of "privacy vs. security" coming? Ask me again in ten years.
 Catherine Pearce is a security consultant at Neohapsis, a security and risk management consulting company specializing in mobile and cloud security services. She spends her time breaking applications and networks, working to secure systems being built, and tinkering with standards to find where the designer missed something. Bred, born, and raised in New Zealand, Kate's a Kiwi who was pulled all the way from Middle Earth to New England a while back. At Neohapsis, she performs varied tasks both on the security "breaker" (assessment) side as well as assisting the builders. Additionally, she’s part of the Neohapsis Labs team which performs research to further security capabilities and knowledge both in house, for customers, and for the security community at large.
Catherine Pearce is a security consultant at Neohapsis, a security and risk management consulting company specializing in mobile and cloud security services. She spends her time breaking applications and networks, working to secure systems being built, and tinkering with standards to find where the designer missed something. Bred, born, and raised in New Zealand, Kate's a Kiwi who was pulled all the way from Middle Earth to New England a while back. At Neohapsis, she performs varied tasks both on the security "breaker" (assessment) side as well as assisting the builders. Additionally, she’s part of the Neohapsis Labs team which performs research to further security capabilities and knowledge both in house, for customers, and for the security community at large.
Photo credit: YuryZap / Shutterstock